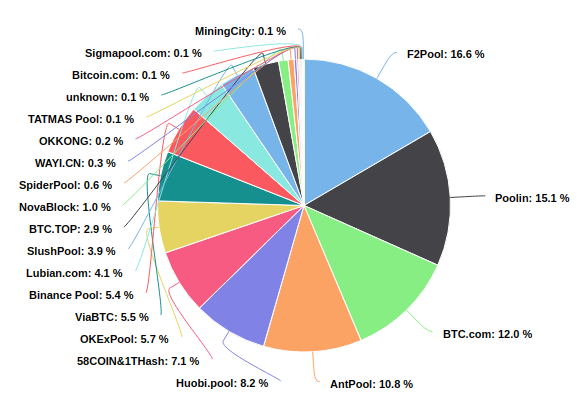
Motivation
Mining pools centralisation, which can lead to censorship and 51% attacks.
Verifiable random functions
Verifiable Random Function (VRF) is a public-key version of cryptographic hash function, and requires a secret key to Hash and Prove, the correspoing public key and proof to Verify.
VRF should satisfy the following properties:
VRF-based mining
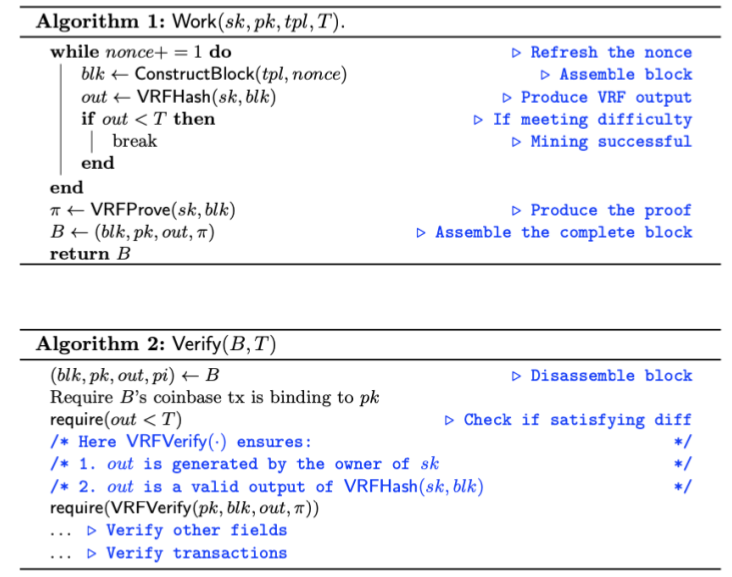
Non-outsourceability analysis
Types of non-outsourceability:
VRF-based mining satisfies punish-mining-reward (miners can still steal reward), but not stealing-unlinkability (stealing is anonymous): a pool operator can outsource different block templates with different secret keys to each miner, and can identify the stealer by the secret key in the transaction stealing the reward.
Related work
Other non-outsourceable mining protocols
Comparison between mining protocols. NSP is short for Non-outsourceable scratch-off puzzle2.| VRF-based mining | NSP-1 | NSP-2 | 2P-PoW3 | |
|---|---|---|---|---|
| Punish-mining-reward | ✓ | ✓ | ✓ | ✓ |
| Stealing-unlinkability | ✗$^\dagger$ | ✗ | ✓ | ✗ |
| No partial outsourcing | ✓ | ✓ | ✓ | ✗ |
| Support randomised signatures | ✓ | ✓ | ✓ | ✗ |
| No complex cryptography | ✓ | ✓ | ✗ | ✓ |
Decentralised mining protocols
Comparison with decentralised mining pools.| VRF-based mining | P2Pool4 | SmartPool5 | BetterHash6 | |
|---|---|---|---|---|
| Complexity | - | Blockchain | Smart contract | - |
| Decentralisation | Mining | Mining | Mining | Select txs |
1. Micali, S., Rabin, M., Vadhan, S.: Verifiable random functions. In: 40th Annual Symposium on Foundations of Computer Science (Cat. No. 99CB37039). pp. 120–130. IEEE (1999). ↩
2. Miller, A., Kosba, A., Katz, J., Shi, E.: Nonoutsourceable scratch-off puzzles to discourage bitcoin mining coalitions. In: Proceedings of the 22nd ACM SIGSAC Conference on Computer and Communications Security. pp. 680–691. ACM (2015). ↩
3. “How to disincentivize large bitcoin mining pools” hackingdistributed.com, Ittay Eyal and Emin Gün Sirer, https://hackingdistributed.com/2014/06/18/how-to-disincentivize-large-bitcoin-mining-pools/. Accessed 27 Aug. 2020. ↩
4. “p2pool: Decentralized, DoS-resistant, Hop-Proof pool” Bitcoin Forum, forrestv, https://bitcointalk.org/index.php?topic=18313. Accessed 27 Aug. 2020. ↩
5. Luu, L., Velner, Y., Teutsch, J., Saxena, P.: Smartpool: Practical decentralized pooled mining. In: 26th {USENIX} Security Symposium ({USENIX} Security 17). pp. 1409–1426 (2017). ↩
6. “BetterHash Mining Protocol(s)” BIPs, Matt Corallo, https://github.com/TheBlueMatt/bips/blob/betterhash/bip-XXXX.mediawiki. Accessed 27 Aug. 2020. ↩